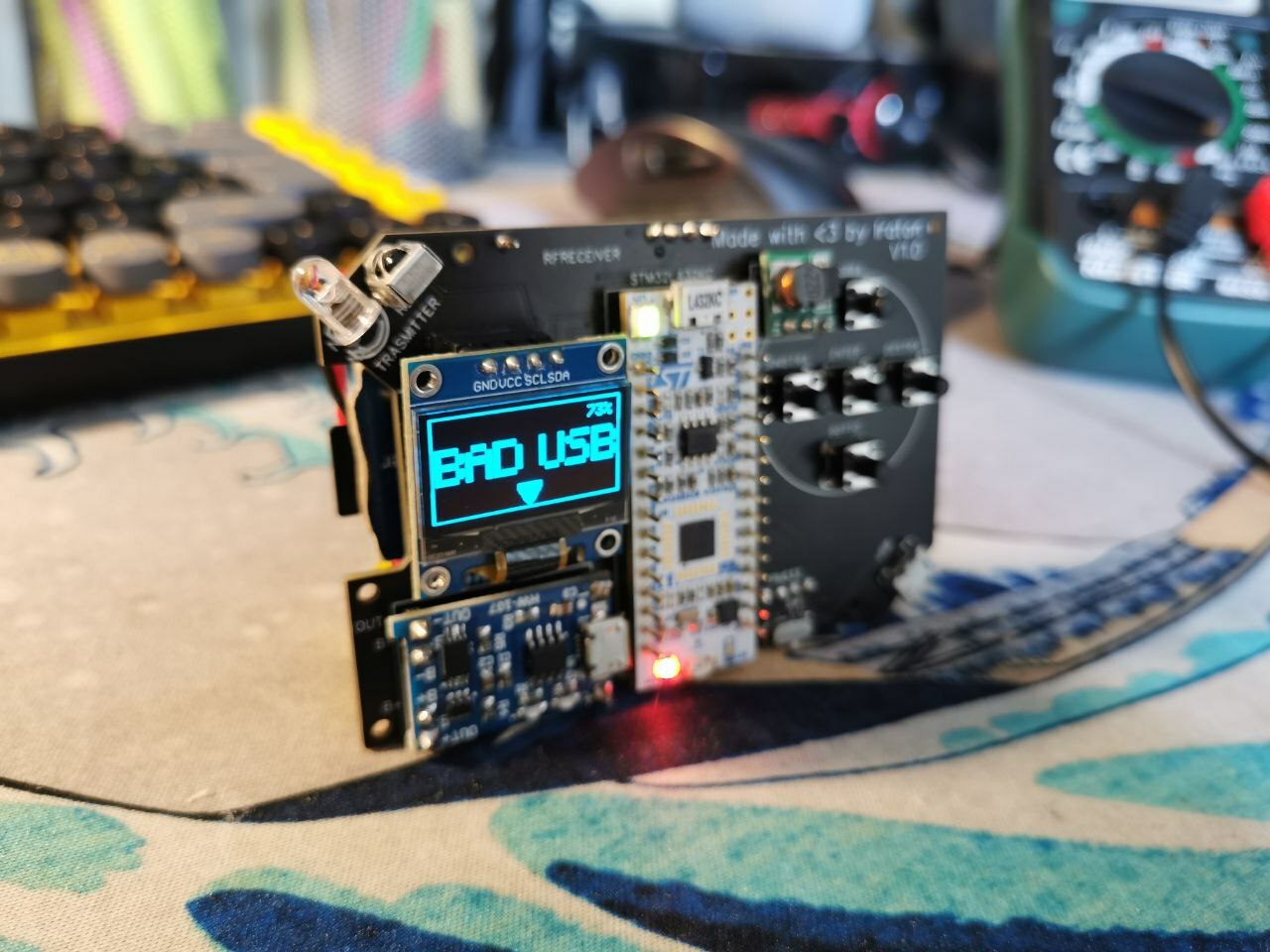
Lilbits: Perplexity’s AI-based web browser, an open source Flipper Zero clone, and another Ryzen AI Max+ 395 mini PC
AI company Perplexity has officially entered the browser business. While the Comet web browser is based on Google’s open source Chromium browser, it’s built to let AI do a lot of the work for you. Instead of entering a URL or typing a search query, you can tell the browser what you’re looking for by text or voice and it will try to find it for you. It can also summarize the content of […]
#ai #android #aoostar #aoostarNex395 #clockworkpiUconsole #comet #computeModule #flipperZero #flopperZiro #google #hackingTool #lilbits #miniPc #notificationOrganizer #notifications #openHardware #radxaCm5 #strixHalo #webBrowsers